The AI
Workforce for Product Security.
Nullify reasons and acts like a human security engineer to replace over 4 tools and the humans required to operate them.
Find all bug classes including business logic flaws
Investigate and auto-triage every bug for proof-of-exploit and impact
Mass auto-resolve vulnerabilities within SLA
Learn from feedback and continuously adjust to your environment
TRUSTED BY INNOVATIng SECURITY TEAMS
.svg)




Nullify creates the outcomes of a fully ramped security team.
By replicating the reasoning of human security engineers, Nullify finds business logic flaws, triages out false positives, prioritizes the vulnerabilities that are exploitable, and routes one‑click fixes to the developers.
454
vulnerabilities auto-resolved by Nullify.
41,757
hours saved triaging vulnerabilities.
89
percent average merge-ready rate for vulnerability fix PRs.
923
exploit hypotheses generated.
Reproducible proof-of-exploits only AI can find.
Nullify reasons through access patterns, code and business logic to find vulnerabilities others can’t — including cross-tenant abuse, authorization bypass and more.
Context-rich triage, proof-backed priorities.
Nullify investigates whether a bug can be exploited based on real cloud reachability, access permissions, and runtime exposure, then determine impact from organizational context.
Get to zero faster — without the back and forth.
Campaigns identify the best owner for every fix, open merge-ready fix PRs, and escalate unmerged fixes in Slack to keep you within SLA — without the human babysitting.
A fleet of AI workers that onboard, reason and act like a human security engineer - but work 24x7 with machine speed.
.webp)

.webp)
.webp)
%20(1).png)
Always on, always adapting.
Nullify understands your environment and apply human-like reasoning to autonomously find, triage, assign and fix exploitable vulnerabilities.
.webp)
TRIAGE
Every finding scored like your team would.
Nullify evaluates each vulnerability by reasoning through exploitability — using runtime reachability, network exposure, and AWS context. It then assesses impact based on your org’s unique risk model stored in Vault: from sensitive repos to VMF-defined priorities. Every triage call is backed by code.
CAMPAIGN
From backlog to merged fix — automatically.
Campaigns bundle validated vulnerabilities into targeted resolution drives. Nullify selects issues from Jira, identifies the right developer, raises merge‑ready PRs in GitHub, refines fixes from CI logs, escalates in Slack as deadlines approach, and closes the loop when merged — driving measurable SLA compliance and backlog burn‑down without manual chasing.
.webp)
.webp)
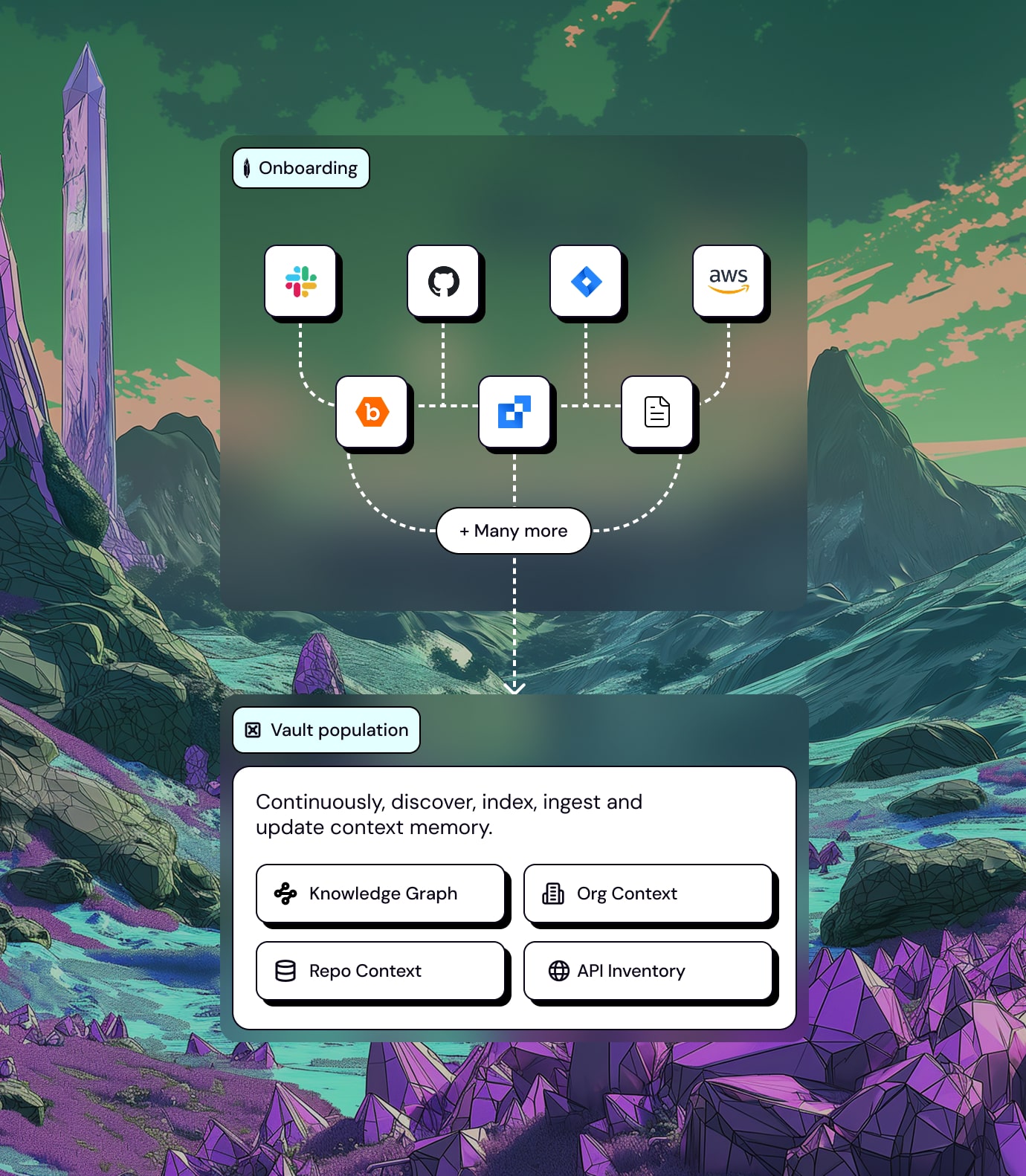
VAULT
Where your org’s tacit knowledge becomes expert reasoning.
Vault is Nullify's long‑term memory — continuously ingesting your unstructured security knowledge: VMF policies, bug bounty reports, cloud architecture, and repo metadata. Nullify use this context to make smarter decisions: suppressing non‑issues, escalating what matters, and adapting their logic to your unique risk posture. Over time, Vault becomes the shared memory that makes Nullify system smarter — without needing to be told twice.
ASSESSMENTS
Watch AI discover and prove business logic flaws
Nullify generates exploit hypotheses by reasoning through code logic, access control, and cloud identity structure. Each hypothesis is tested through real attacks, with only successful, impact-verified findings escalated. Every report includes full proof-of-exploit: the path taken, the inputs used, and where in the code it was triggered.

%20(1).png)
Replace over 4 tools and the human hours they waste.
Simple, usage-based plans designed for small and growing security teams.
Full coverage for less than one security hire.
Automate your entire Product Security program — from detection to fix — without hiring another engineer.
$6000 /month

Find code, dependency, secrets, APIs, and container risks

Code-to-cloud exploit and impact analysis triage (all finding types)

Validation of hardcoded secret credentials

Mass auto-resolution via Jira, GitHub, and Slack (Campaigns)

Business logic flaw detection (auth, access, and more)

Vault for long-term memory of agents
50k tokens included/year
Consumed on every generation of an exploit hypothesis, Vault updates, investigations, and more.
Purpose-built automation for complex enterprise security programs.
Orchestrate exploit discovery and interface with complex engineering orgs to remediate.
Custom pricing

Find code, dependency, secrets, APIs, and container risks

Code-to-cloud exploit & impact triage (all types)

Validation of hardcoded secret credentials

Mass auto-resolution via Jira, GitHub & Slack (Campaigns)

Business logic flaw detection (auth, access & more)

Vault for long-term memory of agents
%20(1).png)

